This topic discusses the following aspects in detail:
- Researching OS vendor sites, technical specifications, and system requirements
- Comparing and contrasting different OSs according to organisational procedures
- Determining licensing, hardware, and security requirements
- Selecting the most appropriate OS for specific operations
- Providing OS recommendations to relevant personnel.
Watch - Operating Systems 1 - Introduction (3:37 minutes)
Watch this overview to kick start your knowledge of OS:
What is server OS?
A server operating system (OS) is specifically designed to run on servers. It is a more advanced version of a standard OS, offering enhanced features and capabilities to provide various services to client machines connected to it.
A server OS supports software, advanced hardware, and network configurations, facilitating the installation and use of business and online web applications. It also manages and monitors client devices. Most processes in a server OS are initiated by OS commands, and it handles a range of administrative tasks.
Servers may perform various services depending on the client's needs. For example, a web server delivers web resources such as web pages in response to client requests. Similarly, a server OS can support other types of servers: a database server manages databases, while a file server provides file access to connected devices.
Features of a Server OS
Some key features of a server OS include:
- Access Options: The server can be accessed via both a Graphical User Interface (GUI) and Command-Line Interface (CLI).
- Client Management: Controls and monitors client computers and their OSs.
- Application Support: Facilitates the installation and use of web and business applications.
- Process Execution: Executes most processes via OS commands.
- Central Management: Provides a central interface for managing users, implementing security, and performing other administrative tasks.
Operating systems (OSs) define how a computer is to:
- store files
- switch between different applications
- manage memory
- keep itself secure
- interact with peripherals (e.g. printers and cameras).
Some OSs are designed by groups of people worldwide, like the open-source, freely available operating system, Linux. In contrast, others are commercial products created and maintained by single companies, such as Microsoft's Windows and Apple's macOS. Although Windows programs are not natively compatible with macOS, there are various methods to run them on a Mac, such as through virtualisation, compatibility software, or dual-booting.
Different OSs run on different types of hardware. For example, iOS is designed for iPhones and iPad tablets, while Mac desktops and laptops use MacOS. Your computer or smartphone comes equipped with an OS, but you can install another one in some cases (permissions also look different on an Android phone than on an iPhone).
Applications are designed to run on specific OSs to accomplish tasks like:
- browsing the internet (requiring Firefox, Google Chrome or Safari)
- editing documents (requiring Microsoft Word or Google Docs)
- playing games (like PC Building Simulator, you will need an environment to run and perform its task).
Features and functions of an OS
The juggling act of multitasking by the OS is like an octopus, keeping your computer running smoothly by multitasking in the background.
Watch - Multitasking Operating Systems (5:10 minutes)
The following video describes the functions and features of an OS in detail. Were you familiar with all of the functions and features of an n OS?
There are numerous management modules within an operating system, each serving a specific purpose, including:
- Process management
- Memory management
- File management
- Device management
- I/O System management
- Secondary-storage management
- Security management
- Command management
- Networking management
- Communication management
- Job accounting.
Types of operating systems
Operating systems (OS) are fundamental components of modern computing systems. They serve as the intermediary between computer hardware and the applications that users interact with, managing resources and providing a user-friendly environment. Understanding the various types of operating systems is crucial for grasping how computers and devices function.
Similarities in Operating System Workflow
In all OS categories, there is a common workflow of having instructions sent by a user through an application, communicated by the OS and translated into the hardware. This workflow is bi-directional (see below).
You will also notice that OSs are designed with a specific purpose in mind, whether based on a particular user group or segments of the market, a field or industry, or even to achieve a set of tasks.
All of the OSs are also derivatives of a parent source code (or the kernel, a computer program at the core of a computer's operating system), as shown in the OS family tree below.
OS family tree
As we can see from the OS family tree, operating systems (OSs) can be categorised into various types based on different criteria. While categorisation helps in understanding the broad classifications, there are many alternatives within each category, reflecting the diversity and specialisation of OSs:
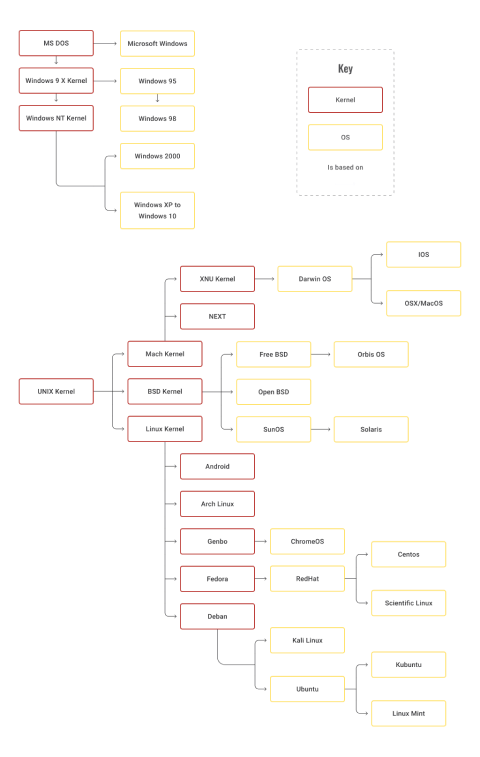
Here are some common categorisation methods:
- Distribution Model: Refers to how OSs and their resources are distributed and accessed, as well as how they are licensed and delivered. This includes:
Network Distribution:
- Client-Server: OSs in this model manage services and resources on a central server, which clients access over a network. Examples include Windows Server and UNIX-based systems used to manage network services.
- Peer-to-Peer (P2P): In this model, systems act as both clients and servers, sharing resources directly with other peers without a central server. Examples include some Linux configurations used in decentralised networks.
Licensing and Delivery:
- Open-Source: OSs that are freely available and can be modified and distributed by anyone, such as various Linux distributions.
- Proprietary: OSs that are owned and controlled by a single company, with restricted access to source code, such as Windows and macOS.
- Purpose and End-User Model: Differentiates OSs based on their primary use and target audience, such as desktop OSs (e.g., macOS), server OSs (e.g., Windows Server), or embedded OSs (e.g., Android for IoT devices).
- User Interface Model: Categorises OSs according to their user interfaces, including command-line interfaces (CLI) (e.g., UNIX) and graphical user interfaces (GUI) (e.g., Windows).
- Portability and Compatibility Model: Focuses on how easily an OS can be adapted to different hardware platforms or its compatibility with various software applications. For example, some OSs are designed to be highly portable across multiple hardware architectures (e.g., Linux), while others are more hardware-specific (e.g., macOS).
We will look at categorising it in the following ways:
- Distribution model
- End-user and main purpose model
- User interface model
- Portability model.
Client/Server
The OS can also be categorised by its distribution model:
- client OS
- server OS.
Differences between client OS and server OS
What is a Client OS?
A client OS is an operating system designed for use on desktop computers, laptops, smartphones, and other portable devices. It manages hardware components such as printers, monitors, and cameras and is typically used by individual users. Client OSs are designed to interact with server OSs to acquire various services. Some examples of Client OSs: Windows, macOS, and Android.
Key Characteristics of Client OS:
- Single-User Focus: Client OSs are primarily designed to support one user at a time, although they can handle multiple processes simultaneously.
- Application Support: They provide support for a range of applications suitable for personal or professional use.
- Hardware Integration: Client OSs manage hardware components like printers, monitors, and cameras.
- Cost and Efficiency: Client OSs are usually designed to be cost-effective and efficient for personal or small business use.
Other Features of Client OS:
- Single-User Support: Designed to accommodate individual user needs.
- Desktop and Portable Device Compatibility: Operates on a variety of devices including desktops, laptops, and smartphones.
- Variety of Desktop Environments: Supports different desktop environments or graphical user interfaces, depending on the OS.
- Security Features: May include security features like encryption, but specifics vary (e.g., BitLocker is available in Windows but not in all client OSs).
- Storage Management: Provides storage solutions suitable for personal or professional use.
Additional Features of a Server OS:
- High Availability and Redundancy: Server OSs often include features to ensure high availability, such as failover clustering and load balancing. These features help minimise downtime by automatically redirecting traffic to another server if one fails.
- Scalability: Server OSs are designed to scale easily, supporting the addition of more resources (like CPU, memory, or storage) and handling increased workloads without compromising performance.
- Virtualisation Support: Many server OSs have built-in support for virtualisation, allowing them to host and manage multiple virtual machines (VMs) on a single physical server. This improves resource utilisation and flexibility.
- Security and Compliance: Advanced security features are integrated, such as firewall management, intrusion detection/prevention systems (IDS/IPS), encryption, and access control lists (ACLs). These features help protect data and ensure compliance with industry regulations.
- Automated Updates and Patching: Server OSs often include tools for automating software updates and security patches, reducing the risk of vulnerabilities due to outdated software.
- Resource Management: The OS can allocate and manage resources (like CPU, memory, and disk space) more efficiently to ensure that critical applications have the necessary resources.
- Centralised User and Group Management: Provides robust tools for managing user accounts, groups, and permissions across the network, ensuring secure and efficient access to resources.
- Backup and Recovery: Server OSs typically have built-in features or support for backup and recovery, allowing data to be easily restored in the event of a failure or data loss.
- Support for Multiple Network Protocols: Server OSs support various network protocols (such as TCP/IP, HTTP, FTP, SMB) to ensure compatibility with different types of client devices and services.
- Remote Management and Monitoring: Enables administrators to remotely manage and monitor the server, often through web-based interfaces, remote desktops, or specialized management software.
- Advanced File System Support: Server OSs often support advanced file systems that are optimised for performance, security, and reliability, such as NTFS (Windows) or ext4/Btrfs (Linux).
- Advanced Networking Capabilities: These include features like DHCP, DNS, routing, and VPN support, which help manage and secure network traffic.

'System requirements' identify the requirements a system needs for hardware and software applications to run smoothly and efficiently.
System requirements can be categorised into:
- software system requirements
- hardware system requirements.
Failure to meet these requirements can result in installation or performance problems--the former may prevent a device or application from getting installed, whereas the latter may cause a product to malfunction, perform below expectation, or even hang or crash.
For packaged products, system requirements are often printed on the packaging.
The system requirements are usually indicated on the download page for downloadable products.
Software system requirements
System requirements can be broadly classified as:
- functional requirements
- data requirements
- quality requirements
- constraints.
They are often provided to consumers in complete detail.
Understanding System Requirements
When developing or evaluating an operating system or any software system, it’s crucial to understand the various types of requirements that must be met to ensure the system’s effectiveness and efficiency. System requirements can be broadly classified into four categories: functional requirements, data requirements, quality requirements, and constraints. Each category plays a vital role in defining the system’s capabilities and limitations.
1. Functional Requirements
Functional requirements describe what a system should do. They specify the functions, features, and interactions the system must support. Essentially, these requirements define the specific tasks and operations the system must perform to meet user needs and achieve its intended purpose.
Examples:
The system must allow users to log in using a username and password.
The operating system must support multi-window functionality.
The application must be able to process transactions and generate receipts.
Functional requirements are often expressed in terms of use cases, scenarios, or user stories, outlining how the system should respond to various inputs and conditions.
2. Data Requirements
Data requirements pertain to the information that the system needs to operate effectively. This includes the types of data the system will handle, how data will be stored, retrieved, and manipulated, and any specific data integrity or security considerations.
Examples:
The system must store user profiles with fields for name, email, and contact information.
The application must support the retrieval and display of data from a database.
Data must be encrypted during transmission to ensure security.
Data requirements ensure that the system can manage and process the necessary information accurately and securely.
3. Quality Requirements
Quality requirements focus on the attributes and performance criteria of the system that affect its usability and reliability. These requirements define the standards the system must meet to provide a satisfactory user experience and to operate efficiently under various conditions.
Examples:
The system must be capable of handling 1000 concurrent users without performance degradation.
The application should respond to user inputs within 2 seconds.
The system must have an uptime of 99.9% to ensure high availability.
Quality requirements address aspects such as performance, reliability, scalability, usability, and maintainability, helping to ensure that the system meets user expectations and operational demands.
4. Constraints
Constraints are limitations or restrictions that affect the design and implementation of the system. These can be imposed by external factors such as hardware limitations, regulatory requirements, budget constraints, or organizational policies. Constraints define the boundaries within which the system must operate.
Examples:
The system must be compatible with existing hardware and software configurations.
The application must comply with industry regulations and data protection laws.
The development budget is limited to $500,000.
Constraints help to ensure that the system operates within defined limits and adheres to necessary standards and policies.
By understanding and addressing these categories of system requirements—functional, data, quality, and constraints—developers and stakeholders can ensure that the system meets its intended goals, operates efficiently, and adheres to all necessary guidelines and limitations. This comprehensive approach to defining requirements helps in creating robust, reliable, and effective systems.
System requirements can also be expressed as the:
- minimum requirement is the most basic--enough for a product to install or run, but performance is not guaranteed optimal (you may experience slower than acceptable performance when trying to complete more complicated tasks or if using more than one piece of software simultaneously)
- recommended requirement ensures a smooth operation.
In addition to the above, the requirements may also specify additional software dependencies (e.g., libraries, driver version, framework version).
Software--commonly known as programs or applications (apps)--consists of all the instructions that tell the hardware how to perform a task. These instructions come from a software developer in the form that will be accepted by the platform (OS and CPU) that they are based on.
Software compatibility
The compatibility of the software will vary as the design of the software and the OS differ.
For example, a program designed for the Windows OS will only work for that specific OS; therefore, software designed for Windows 10 may experience a compatibility issue when running under Windows 2000 or NT.
Software system classes
The software can perform many tasks instead of hardware, which can only perform mechanical tasks. The software provides the means for accomplishing multiple different tasks with the same basic hardware.
Practical computer systems divide software systems into 2 major classes:
System software
- Runs the computer hardware and computer system itself.
- System software includes operating systems, device drivers, diagnostic tools and more.
- System software is almost always pre-installed on your computer.9
Application software
- Allows users to accomplish one or more tasks.10
- Application software includes word processing, web browsing and almost any other task for which you might install the software.
- Application software is not always pre-installed on computer systems.
The following video, Computer Basics: Understanding Applications, explains what an 'application' is.
Common types of application software are:
- document processing programs
- accounts software
- billing software
- payroll software
- database software
- asset management software
Hardware system requirements
'Hardware' refers to the physical elements of a computer, also called the machinery or the equipment of the computer.
Examples of hardware in a computer are the: keyboard, monitor, mouse and central processing unit. However, most of a computer's hardware components are stored internally, surrounded by the computer's case.
Hardware system requirements often specify:
- OS version
- processor type
- memory size
- available disk space
- additional peripherals, if needed.
Some hardware/software manufacturers provide an 'upgrade assistant' program that users can download and run to determine whether their system meets a product's requirements.
Most hardware only has OS requirements or compatibility. For example, a printer may be compatible with Windows XP but not with newer versions of Windows (like Windows 11, Linux or macOS).
For a hardware device to be compatible with your computer, it is up to the manufacturer to release drivers. Many manufacturers release updated drivers to fix problems with older drivers and often release drivers for newer or alternative OSs.

Various aspects of hardware requirements
Architecture
The OS depends on the hardware platform; however, some applications can be run on different platforms, called 'cross-platform applications'.
The source code of Java applications is half compiled, allowing them to be independent on different hardware architectures.
Java applications can be installed with Java Virtual Machine (JVM) on different OSs. Although they are cross-platform compatible, they will run slower than an equivalent application that was fully compiled.
Processing power
The speed of the central processing unit (CPU) is a fundamental system requirement for any software.
Most CPU processing power is defined by its model and clock speed. Other features that can also affect the processing power of the CPU are the CPU cache and the number of CPU cores.
The definition of CPU performance is often confusing; for example, AMD Athlon and Intel Pentium CPUs at similar clock speeds often have different performances.
The following video explains the duopoly of Intel and AMD as the 2 major CPU producers.
Memory
All software, when run, resides in the random access memory (RAM) of a computer.
Memory requirements are defined after considering the application's demands, OS, supporting software and files, and other running processes. When defining this requirement, the optimal performance of other unrelated software running on a multi-tasking computer system is also considered.
Secondary storage
Data storage device requirements vary, depending on the size of software installation, temporary files created and maintained while installing or running the software, and possible use of swap space (if RAM is insufficient).

Display adapter
Software requiring a higher than average graphics display performance (such as graphics editors and high-end games) often define high-end video cards in their system requirements.
Peripherals
Some software applications need to make extensive and special use of certain peripherals, demanding the higher performance or specific functionality offered by them (such as CD-ROM drives, keyboards, pointing devices, network devices, etc.).
Example of system requirements
System requirements for installing Windows 10
These are the basic requirements for installing Windows 10 on a PC. If your device does not meet these requirements, you may not be able to install Windows 10 and might want to consider purchasing a new PC.
| Processor: | 1 gigahertz (GHz) or faster processor or System on a Chip (SoC) |
|---|---|
| RAM: | 1 gigabyte (GB) for 32-bit OS or 2 GB for 64-bit OS |
| Hard drive space: | 16 GB for 32-bit OS 32 GB for 64-bit OS |
| Graphics card: | DirectX 9 or later with WDDM 1.0 driver |
| Display: | 800x600 |
| Internet connection: | Internet connectivity is necessary to perform updates, download, and take advantage of some features. Windows 10 Pro in S mode, Windows 10 Pro Education in S mode, Windows 10 Education in S mode and Windows 10 Enterprise in S mode requires an internet connection during the initial device setup (Out of Box Experience or OOBE), as well as either a Microsoft account (MSA) or Azure Activity Directory (AAD) account. Switching a device out of Windows 10 in S mode requires internet connectivity.16 |
Upgrading to Windows 11
When Microsoft released Windows 11 it was rolled out as an upgrade to those who had earlier versions of Windows. They described it as having 'easy-to-use tools that can help you optimise your screen space and maximise your productivity'.
You could only upgrade your system if your device was running Windows 10, version 2004 or later. The process to update your OS for free was in Windows Update in Settings > Update and Security and met the following requirements:
| Processor: | 1 gigahertz (GHz) or faster processor with 2 or more cores on a compatible 64-bit processor or System on a Chip (SoC) |
|---|---|
| RAM: | 4 gigabyte (GB) |
| Storage: | 64 GB or larger storage device |
| System firmware: | UEFI, Secure Boot capable |
| TPM: | Trusted Platform Module (TPM) version 2.0 |
| Graphics card: | Compatible with DirectX 12 or later with WDDM 2.0 driver |
| Display: | High definition (720p) display that is greather than 9" diagonally, 8 bits per colour channel |
| Internet connection: | Internet access is required to download updates. A Microsoft account is also necessary to take advantage of some features and is a requirement of Windows 11 Home edition. |
Operating System Security Requirements
'OS security' is the process of ensuring the computer, and its systems and data maintain integrity, confidentiality, and availability.
This involves specific steps or measures to protect the OS (from threats, viruses, worms, malware or remote hacker intrusions) through many preventive-control techniques which safeguard the computer data being stolen, changed or deleted.
It also allows different applications and programs to continue to perform required tasks while stopping unauthorised interference.
OS security may be approached in numerous ways, including adherence to the following:
- performing regular OS patch updates
- installing updated antivirus engines and software
- inspecting suspicious network traffic through the firewall
- creating secure accounts with required privileges only (i.e. user management).
Basic requirements of a secure operating system
Mandatory security
Mandatory security is a built-in mechanism, or logic, within the OS—often called a 'system security module' or 'system security administrator'.
The efforts to develop secure operating systems can be dated to the earlier days of OS development.
Its function is to implement and control:
- the definition and assignment of security attributes
- their actions (security policies) for every operation or function provided by the system.
Generally, mandatory security will require:
- main security controls, such as:
- permission or access authorisation
- authentication usage
- cryptographic usage
- subsystem-specific usage
- a policy independent security labelling and decision-making logic:
- the OS implements the mechanism
- the users or applications define the policies;
Imagine a system that needs to handle security in a flexible way. Instead of relying on a fixed set of rules (policies), this system uses a method that can adapt to different situations.Security Labelling: This means tagging or marking data with labels that indicate its security level, like "Confidential" or "Public."
- Decision-Making Logic: This is how the system decides what actions to take based on those labels, such as who can access the data.
-
Policy-Independent means the system does not depend on specific security rules that might change over time. Instead, it uses a more adaptable approach that can handle various security requirements as needed.
- Enforcement of access control for all operations, requiring:
- Control over the propagation of access rights
- Enforcement of fine-grained access controls
- Support for the revocation of previously granted access rights
Trusted Sources
A 'trusted path' is a mechanism by which a trustworthiness relationship is established among users and application software so that:
- a user or application may directly interact with trusted software, which can only be activated by either a user or trusted software
- a mutually authenticated channel is needed to prevent the impersonation of either party
- the mechanism must be extensible to support the subsequent addition of trusted applications.
Support of various security policies
Traditional Multiple Access Control (MAC), such as Multi-Level Security (MLS), usually bases its security decisions on two different systems:
- clearances for subjects
- security labels for objects.
The systems are normally too restricted to serve as a general security solution. A secure architecture requires flexibility for support of a wide variety of security policies:
- Separation of security policy logic from the mechanism of policy enforcement: this is to ensure a system can support various security policies.
- Support policy definition and policy changes: with well-defined policy interfaces and formats.
- Provider of default security behaviour of the system: to maintain tight system security without requiring detailed system configuration.
Assurance
This is a process or methodology to verify the design and implementation of the system that should behave as it claims to be and meet the security requirements.
- The process generally involves 2 elements:
- statement of the security properties that a system is claimed to satisfy
- some kind of argument or evidence that the system does satisfy those properties.
- The structure of such systems normally requires a small security kernel or module so that the system behaviour would be relatively easy to be verified.
Covert channels
One of the concerns for a secure OS is the so-called covert channels, which are the means to circumvent the security barrier enforced by the system to prevent the passing of information from one security domain to a less secure domain.
There is no general way to prevent all covert channels.
It is more practical to introduce enough 'noise' or reduce the bandwidth of such channels in the system so that they won’t be useful to an intruder.
Most of the time, when organisations are considering implementing a new OS, they will take note of the following aspects in addition to technical specifications:
- what applications will run
- what features are available
- whether their IT technicians have existing knowledge on the OS or need to upskill.
Organisations rarely depend on the technical specification of a system or product alone.
A 'specification document' defines information about the technical, development and procedures related to the requirements it outlines.
A 'technical specification' is more detailed and includes a document that defines the requirements for a project, product or system and outlines how you will address a technical problem by designing and building a solution for it.
This document also provides developers and other stakeholders with information on business requirements, internal standards and best practices.
It’s sometimes also referred to as:
- a technical design document
- a software design document
- an engineering design document.
Usually, this document is written by the engineer who will build the solution or be the point person during implementation. Still, it can be written by technical leads, project leads or senior engineers for larger projects.
It will show the engineer’s team and other stakeholders the design, work involved, impact, and timeline of a feature, project, program, or service.

Microsoft Windows OS
Microsoft Windows is the dominant commercial PC OS--estimated to be installed on 90 per cent of the world's desktop and laptop computers. The Windows Server OS is also widely used on private network servers and internet servers running web, email and social networking apps.
Windows and Windows Server® have been released in several versions (like most software). Historically, a new version would have to be purchased, though upgrade discounts were usually available. A new version may introduce significant changes in desktop styles and Windows user interface and add new features and support for new types of hardware.
A new version may not be compatible with hardware and software applications designed for earlier versions. One of the main functions of an OS is to provide an interface (or shell) between the user and the computer hardware and software.
Windows has several interface components designed for general use and more technical configuration and troubleshooting.
The top level of the user interface is the 'desktop'. This is displayed when Windows starts, and the user logs on. The desktop contains icons to launch applications and possibly user data files. The desktop also contains the Start Menu (or Start Screen) and taskbar used to launch and control applications.
Microsoft Windows versions
Let's start by looking at the most popular versions of Windows currently in use.
Windows 10 was first released in 2015 and aims to provide a consistent user experience across different devices (including desktop PCs, laptops, tablets and smartphones).
It retains the user desktop and taskbar familiar from legacy versions when installed to a PC or laptop. Still, it uses a touch-optimised Start Screen interface to access apps and programs. This replaces the old Start Menu. As well as shortcuts, the Start Screen can display app tiles containing live or actively updated content. (These app tiles are fully customisable.)21
Versions and Editions in Windows Operating System
Microsoft use major versions to classify different OS products. For example, Windows 8, Windows 10 and Windows 11 are different Windows major versions of the operating system.
Each version of Windows also provides several editions with prices and features differences to suit various needs of their customers. For example, Windows 11 comes with home, professional and enterprise editions and the home edition provide the most fundamental features for the home users with lower price.
On the other hand, the Windows 11 professional edition provide more features such as Hyper-V, domain join and bit-locker drive encryption etc. to their business users with higher price.
32-bit and 64-bit Windows
Most versions and editions of Windows are available as 32-bit or 64-bit (x64) software (Windows 11 does not support 32-bit).
Most 32-bit applications can run on 64-bit versions of Windows, though there may be some exceptions (you should check with the software vendor). However, the reverse is not true--a 32-bit version of Windows cannot run 64-bit application software.
The 64-bit version of Windows also requires 64-bit hardware device drivers installed. If the hardware manufacturer did not produce a 64-bit driver, the hardware device would not be usable in Windows.
Windows system limits
Different editions of Windows support different hardware and features, as shown in the table below.
| Feature | Home | Pro | Education | Enterprise |
|---|---|---|---|---|
| SMP (Multiple CPUs) | No | 2-way | 2-way | 2-way |
| Multicore | Yes | Yes | Yes | Yes |
| RAM limitations (32-bit) | 4 GB | 4 GB | 4 GB | 4 GB |
| RAM limitations (64-bit) | 128 GB | 2 TB | 2 TB | 6 TB |
OS lifecycles
An 'end-of-life system' is one that its developer or vendor no longer supports.
End-of-life systems no longer receive security updates and may pose critical vulnerabilities to a computer system.
Microsoft products are subject to a support lifecycle policy. Windows versions are given 5 years of mainstream support and 5 years of extended support (during which only security updates are shipped).
Support is contingent on the latest ServicePack (SP) being applied (non-updated versions of Windows are supported for 24 months following the release of the SP). Windows 10 retirement schedules for feature updates—referred to as 'end of service'—are 18 months, except for September updates for Education/Enterprise editions (which are supported for 30 months).
To determine when Microsoft products will be retired or how long specific products will be supported, use the Microsoft Product Lifecycle Search tool — a great resource to bookmark.
When you plan to install a new version of an OS as an upgrade, you must check that your computer meets the hardware requirements for the new version.
As OS software such as Windows 10 moves towards more of a service model, with quite frequent feature updates, it could be the case that an update has system requirements that are different from the original.
Plus, Microsoft points out that the core hardware requirements for Windows 10 are the same as those for Windows 7.
Other factors might impact your ability to apply a feature update, including third-party driver or applications software support.
Windows in the corporate world
The principal distinguishing feature of the Professional/Pro, Enterprise, Ultimate and Education editions (regardless of version) is the ability to join a domain network.
A personal user or small business owner can just administer each machine they own individually. It is necessary to manage user accounts and system policies centrally on a corporate network because there are more machines to manage and higher security requirements. This centralised management is provided by joining each computer to a domain, where the accounts are configured on Domain Controller (DC) servers.22
Other notable corporate features
BitLocker: Enables the user to encrypt all the information on a disk drive.
'Encryption' means that data on the device is protected even if someone steals it (as long as they cannot crack the user password). BitLocker is included with Windows 7 Enterprise and Ultimate, Windows 8 Pro and Enterprise and Windows 10 Pro, Enterprise and Education editions.23
Encrypting File System (EFS): Where BitLocker encrypts an entire drive, EFS can be used to apply file- or folder-level encryption. EFS is included with Windows 7 Professional, Enterprise and Ultimate, Windows 8 Pro and Enterprise and Windows 10 Pro, Enterprise and Education editions.24
BranchCache: An enterprise might have computers installed at different geographic locations needing to view and update data at a central office. The Wide Area Network (WAN) links from each location to the office might be quite slow. It can be useful for remote computers to share access to a single cache of data from shared folders and files or document portals such as SharePoint sites.
This reduces the amount of WAN traffic because each client does not have to download a copy individually. BranchCache is supported on Windows 7 Enterprise and Ultimate, Windows 8 Pro and Enterprise and Windows 10 Pro, Enterprise and Education editions.25
Advantages
Ease of use
Users familiar with earlier versions of Windows will probably also find the more modern ones easy to work with. This is because of many things—from the standardised look and feel of almost all programs written for Windows to the way the file system has been presented ever since the days of MS-DOS (disk A:\, disk C:\, etc.). This is one of the main reasons Windows users are often reluctant to switch OS.26
Available software
There is a huge selection of software available for Windows. This is both due to, and the reason for, Microsoft's dominance of the world market for the PC OS and office software. If you are looking for an application to suit your business needs, the chances are that if it exists, there will be a Windows version of it available somewhere.27
Backwards compatibility
Suppose you're currently using an older version of Windows and need something more up-to-date, but you don't want to lose the use of some older programs that are only available for Windows and are critical to your business needs. In that case, the chances are good (although not a certainty) that those programs will also work with a newer version of Windows.28
Support for new hardware
Virtually all hardware manufacturers will offer support for a recent version of Windows when they market with a new product. Again, Microsoft's dominance of the software market makes Windows impossible for hardware manufacturers to ignore. So, if you run off to a store today and buy some random new piece of computer hardware, you'll find that it will probably work with the latest version of Windows.29
Continuous improvement on remote access
Since the Pandemic hit in 2020, the uptake of web-based software has skyrocketed. Once upon a time, Microsoft products could only be bought off the shelves. Nowadays, you will have witnessed personal, educational and professional use and reliance on this software to connect, educate and maintain work communications.
Disadvantages
High resource requirements
Unlike the makers of other OSs, Microsoft requires its customers to invest the most in their computer hardware: a faster processor (the CPU), more internal memory and a larger hard disk. Few people use many of those features, yet everyone is still forced to contend with the additional overhead that is the result.
Closed Source
Troubleshooting problems with Windows would be so much easier for users and support personnel if only they knew what was going on. Unfortunately, only Microsoft has full access to its software's source code, and since no log files are generated, its users are left to try and deduce what causes their problems by trial and error alone. At best, this is time-consuming; while at worst, it can make a program impossible to work with. (See also: 'Shared Source'.)
Poor security
Compared to other OSs, Microsoft's security is weak. The result is that Windows computers are more likely than other systems to be hijacked and used to distribute everything from spam to pornography (Ref: Inquirer) to hate mail. Windows has extensive logging capabilities through Event Viewer, and system administrators can configure detailed logs to track system and network activity.
Windows computers are more likely to be hacked than other OS. The reason is GUI. When you use GUI instead of CLI, it increases the attacking surface.
Previously, you had to run/execute commands directly; however, now you need to double-click an icon to execute most commands. This weakness has been brought about by the use of a GUI. At first, Microsoft Windows Server provided a GUI installation only; but now they have changed the default installation to a core-server installation (installation without GUI) because they realised the GUI left the server exposed to attacks.
Virus susceptibility
The susceptibility of Microsoft's operating systems to computer viruses has often been highlighted as a part of broader security challenges. Historically, due to the widespread use and popularity of the Windows OS, it has been a primary target for virus developers. Consequently, a robust ecosystem of anti-virus software has been developed for Windows platforms.
To protect their systems, businesses must keep their anti-virus software and signature databases up-to-date, as well as regularly apply Microsoft’s security patches. This ongoing investment in security measures is essential not only for Windows but for any operating system to guard against evolving threats.
Case Study
Client problem description
You are advising a customer whose business is expanding. The business owner needs to provide an additional 30 desktop computers, some of which will be installed at a second office.
The business is currently run with a workgroup network of 5 Windows 7 Home Premium desktop computers and 1 file server.31
Question hints
Why might you suggest licenses for an edition of Windows 10 or 11 that supports corporate needs for the new computer and has upgrades for the old computers?
Which specific edition(s) could you recommend?
Considerations
Did you have your answers ready? Let’s compare.
- Without a domain, accounts must be configured on each computer individually.
- With over 30 computers to manage at 2 locations, this would be a substantial task so switching to a domain network, where the accounts can be configured on the server, is likely to save costs in the long term.
- The BranchCache feature would also allow computers at the second office to minimise bandwidth usage when downloading documents (Enterprise edition only) and updates from the main office.
- You can suggest either Windows 10 Pro or Windows 10 Enterprise for use on a domain. As Windows moves towards a service model, subscription-based licensing of the Enterprise edition is becoming the mainstream choice.
Windows and macOS dominate the desktop/workstation/laptop market, but a third 'family' of OSs is widely used on a larger range of devices—Unix.
UNIX
UNIX is the trademark for a family of OSs originally developed at Bell Laboratories in the late 1960s. All UNIX® systems share a kernel/shell architecture, with the kernel providing the core functionality and the interchangeable shells providing the user interface.
Unlike Windows and macOS, UNIX is portable to different hardware platforms—versions of UNIX can run on everything from personal computers to mainframes and many computer processors.
UNIX was developed by various commercial, academic, and not-for-profit organisations.
Linux
Originally developed by Finnish software engineer, Linus Torvalds, Linux® is based on UNIX.
The introduction of Linux resulted in several versions, not all of which are compatible, and many of which are proprietary or contain copyrighted or patented code and/or features. Linux was developed as a fully open-source alternative to UNIX (and, for that matter, to Windows and macOS and iOS).
Linux can be used as a desktop or server OS. There are many distributions (or 'distros'), notably:
- SUSE®
- Red Hat®
- CentOS
- Fedora®
- Debian®
- Ubuntu®
- Mint®.
Each distro adds specific packages and interfaces to the generic Linux kernel and provides different support options.
Linux does not require a graphical interface, though many distros provide one.
IBM®, Sun/Oracle®, and Novell® are among the vendors producing end-user applications for Linux.
It tends to be used in schools and universities more than in business or the home as a desktop OS. As a server OS, it dominates the market for web servers. It is also very widely favoured as the OS for 'smart' appliances and Internet of Things (IoT) devices.
Advantages
Open Source
As mentioned earlier, Linux is an open-source OS. This can come in handy, especially for people who code and need to change how their computer works. It is also free to install and use, unlike Windows or Mac, so it could be a great alternative for someone who is on a budget but needs a computer that can adapt according to their requirements.
Security
One of the best qualities of Linux is that it is extremely secure. Since it is an open-source OS, several developers look out for viruses and potential threats. So, when the code needs to be upgraded or changed, it can be done.
Another reason for this security is that since the number of Linux users is comparatively lower than Windows users, it is not profitable to create viruses for this system. Automatically, lesser viruses equal lesser chances of your system being infected.
Speed
It is a fact that anti-virus programs slow down a system. Since the software constantly updates its database of viruses and checks the system for them, it uses a lot of memory.
Because Linux does not require installing this software, a huge chunk of memory is unused, creating a faster system. On top of that, Linux already works faster than Windows because of its comparatively simpler user interface.
Redesigning
One of the biggest advantages of Linux is that it is very easy to change according to your needs. It is also one reason why it is very popular among programmers. Since you can see the source code for this OS, it is easier and legal (unlike Windows) to change it according to your needs for your system.
Low System Specifications
Another reason why Linux is a better choice is that it works on computers with very low system specifications. If you choose to use an older computer, Linux is a great choice for you. It will run without a problem, unlike Windows or Mac.
Disadvantages
Learning Curve
Learning how to use Linux can take a while, especially if you are used to using another OS and not an open-source OS like Linux. The user experience is different in Linux, so you need to set aside time to learn the system first. This could be frustrating to some people.
Installing Software
A variety of applications that work on Windows or Apple operating systems do not work in Linux. If you are someone who needs to have access to certain applications for your work, you will first want to see if it works in Linux—Microsoft applications are one such example of software that isn’t available for Linux users.
Lack of Games
Statistically, most computer users use either Windows or macOS, so game developers create games suited to these OSs. Linux doesn’t support a lot of popular games. This is one reason why Linux isn’t popular among young users yet.
Hardware Drivers
One of the biggest problems in Linux, as reported by users, is that drivers don’t exist in this OS. Like most software, there are ways to work around that, but problems have been reported when people try to use old hardware or certain other hardware.32
Apple operating systems

It was revolutionary because it came with a graphical user interface when IBM's PC used the command-line/text menu DOS OS. The Mac has never matched Windows' huge user base, although its current incarnation does have a truly devoted following.
Apple Mac OS/OS X/macOS
The main difference between macOS and other operating systems is that the OS is only supplied with Apple-built computers. You cannot purchase macOS and install it on an ordinary PC. This helps make macOS stable but means that there is far less choice in buying extra hardware.
Most Apple devices support Siri®, a voice recognition system and personal assistant.
New versions are released approximately every year with various .x updates. Apple makes new versions freely available, though older hardware devices may not support all the new version features or may not be supported.33
Here is a list of Mac OS, OS X and macOS releases over the years.
| macOS | Latest version |
|---|---|
| macOS Monterey (current) | 12.2.1 |
| macOS Big Sur | 11.6.4 |
| macOS Catalina | 10.15.7 |
| macOS Mojave | 10.14.6 |
| macOS High Sierra | 10.13.6 |
| macOS Sierra | 10.12.6 |
| OS X El Capitan | 10.11.6 |
| OS X Yosemite | 10.10.5 |
| OS X Mavericks | 10.9.5 |
| OS X Mountain Lion | 10.8.5 |
| OS X Lion | 10.7.5 |
| Mac OS X Snow Leopard | 10.6.8 |
| Mac OS X Leopard | 10.5.8 |
| Mac OS X Tiger | 10.4.11 |
| Mac OS X Panther | 10.3.9 |
| Mac OS X Jaguar | 10.2.8 |
| Mac OS X Puma | 10.1.5 |
| Mac OS X Cheetah | 10.0.4 |
Published date: 16 February 2022
Advantages
Comes with useful free productivity apps
The selection of free Apple-developed apps preinstalled in a Mac device or available for downloaded through the App Store is another advantage of macOS. For example, office productivity apps such as Pages, Numbers and Keynote are free; unlike the Microsoft Office Suite apps which are generally sold separately.
Simple and cleaner user interface than windows
When stacked up against Windows, macOS has the advantage of having a user interface that is simpler and more intuitive. Those familiar with the iOS mobile operating system used in iPhones and iPads will find using macOS very familiar. Apps are generally downloaded via the App Store and found in a central location.
Dedicated features for multitasking
Several multitasking features are native to macOS and Mac devices. The OS has a feature for running multiple workspaces similar to opening numerous desktops or home screens. Mac devices have dedicated keys and other hardware inputs such as gestures for switching between apps or workspaces.
Optimised software and hardware due to better integration
Another advantage of macOS is that it runs with fewer, to zero, hiccups. Apple is both a hardware designer and a software developer. Third-party hardware components are selected based on established criteria, while third-party apps undergo tests and verifications for compatibility and security. The strong attention to software-hardware integration results in optimised performance.
Less susceptibility to malware and security issues
Take note that macOS is still susceptible to malware. However, compared to Windows, few types of malware were developed specifically for the macOS.
It is also important to note that Apple regularly provides security updates for the entire operating system and apps. The fact that apps can be (generally) only be downloaded via the App Store means fewer risks of installing other apps from suspicious developers.
Compatibility with other Apple devices and services
Apple has developed and marketed products and services seamlessly compatible with one another. Both macOS and iOS have a near similar user interface and workflow logic. Also, apps developed by Apple and those from third parties have versions available for both macOS and iOS. Files or data are synchronised across devices due to Apple's dedicated and free cloud services.
Disadvantages
Limited and restricted availability of apps
One of the drawbacks of macOS is that it still has a limited number of apps. Note that Windows enjoys a huge selection of apps from different categories and it also has a broader selection of games. macOS is not ideal for gamers.
It is worth mentioning that Windows devices are more accessible than Mac devices; hence, developers prioritise developing for Windows because of the better market reach.
Inflexibility for hardware upgrades and customisation
Although not a direct limitation or disadvantage of macOS, it is still important to mention that Mac devices have a limited option for hardware upgrades.
For instance, the CPU or RAM of a MacBook laptop or iMac desktop cannot be replaced easily because these components are deeply integrated with the entire hardware system. Several Windows computers provide a better level for customisation and upgrades.
It can be very expensive to own a macOS device
MacBook laptops and iMac desktops are very expensive compared to Windows-based counterparts with similar or better hardware specifications. Take note that macOS is exclusive for Mac devices. Hence, another key disadvantage of this OS is that it is very expensive to own.
There are workarounds for installing macOS on non-Apple devices, but this is illegal.
Lacks appeal for hard-core gamers
Remember that macOS has limited game titles and limited hardware upgrades or customisation options. These facts mean that both the OS and Mac devices are not appealing to gamers.
Although high-end Mac devices have capable hardware features, the lack of game titles and the fact that these devices are more expensive than their Windows-based counterparts dissuade gamers and game developers alike. Essentially, macOS is not marketed for gamers.34
Case Study
Client problem description
A customer asks whether an iOS app that your company developed will also work on her Apple macOS computer.
Question hint
What issue does this raise, and what answer might you give?
Considerations
Did you have your answers ready? Let’s compare.
The issue here is compatibility between different operating systems.
Even though Apple produces iOS and macOS using different environments, the iOS app cannot be installed directly. Your company might make a macOS version.
In the latest version of macOS (Mojave), support for native iOS apps is being provisioned, so this might be something you can offer in the future.
Google Android

Unlike iOS, it is an open-source OS based on Linux.
This means that there is more scope for the production of vendor-specific versions by hardware vendors, such as:
- Acer®
- Asus®
- HTC®
- Huawei®
- LG
- Motorola®
- OnePlus
- Oppo™
- Samsung®
- Sony®
- Xiamoi.
Android version updates
Like iOS, Android is updated with new major (1. x) and minor (x.1) versions, each of which is named after some sweet stuff. At the time of writing, current versions include 13 (Tiramisu).
Because handset vendors produce their editions of Android, device compatibility for new versions is more mixed than iOS.
End-of-life policies and update restrictions for particular handsets are determined by the handset vendor rather than the overall Android authority. Companies ordering handsets in bulk as employee devices may be able to obtain their guarantees.35
See the timeline of sweets-inspired version updates in the following table.
| Name | Internal code name | Version number |
|---|---|---|
| Android 1.0 | N/A | 1 |
| Android 1.1 | Petit Four | 1.1 |
| Android Cupcake | Cupcake | 1.5 |
| Android Donut | Donut | 1.6 |
| Android Eclair | Eclair | 2.0 |
| Android Froyo | Froyo | 2.2 |
| Android Gingerbread | Gingerbread | 2.3 |
| Android Honeycomb | Honeycomb | 3 |
| Android Ice Cream Sandwich | Ice Cream Sandwich | 4 |
| Android Jelly Bean | Jelly Bean | 4.1 |
| Android KitKat | Key Lime Pie | 4.4 |
| Android Lollipop | Lemon Meringue Pie | 5 |
| Android Marshmallow | Macadamia Nut Cookie | 6 |
| Android Nougat | New York Cheesecake | 7 |
| Android Oreo | Oatmeal Cookie | 8 |
| Android Pie | Pistachio Ice Cream | 9 |
| Android 10 | Quince Tart | 10 |
| Android 11 | Red Velvet Cake | 11 |
| Android 12 | Snow Cone | 12 |
| Android 12L | Snow Cone v2 | TBA |
| Android 13 | Tiramisu | 13 |
Case Study
Client problem description
You are advising a customer with an older model Android smartphone. The customer wants to update to the latest version of Android but using the update option results in a 'No updates available' message.
Question hint
What type of issue is this, and what advice can you provide?36
Considerations
Did you have your answers ready? Let’s compare.
This is an issue with update limitations.
The market for Android is quite fragmented, and customers must depend on the handset vendor to implement OS updates for a particular model. The customer can check the handset vendor's website or helpline to find out if a version update will ever be supported for that model.
Google Chrome OS
Chrome OS™ is derived from Linux via an open-source OS called Chromium™.
Chrome OS itself is proprietary. Google develops the Chrome OS to run on a specific laptop (Chromebook) and PC (Chromebox) hardware. This hardware is designed for the budget and education markets.
Chrome OS was primarily developed to use web applications. The web application does not require installation, which means you only need to have a browser to run the applications.
It provides a minimal environment compared to Windows, meaning that there is less chance of some other software application or hardware device driver interfering with the browser's function.
There are also 'packaged' apps available for use offline, and Chrome OS can run apps developed for Android.
Licensing, hardware and security requirements
OS licensing
An OS license is a legal instrument (usually by way of contract law, with or without printed material) governing the use or redistribution of the OS.
Under copyright law, all OSs are copyright protected, in both source code and object code forms, unless an OS was developed by the government--therefore, it cannot be copyrighted.
Authors of copyrighted OSs can donate their OSs to the public domain, in which case they are not covered by copyright and, as a result, cannot be licensed.37
A typical OS license grants the licensee, typically an end-user, permission to use one or more copies of an OS in ways where such a use would otherwise potentially constitute copyright infringement of the OS owner's exclusive rights under copyright.
Types of the common software license
Public domain
This is the most permissive type of software license.
When software is in the public domain, anyone can modify and use the software without any restrictions. But you should always make sure it’s secure before adding it to your codebase.
Caution
Code that doesn’t have an explicit license is NOT automatically in the public domain. This includes code snippets you find on the internet!
Permissive
Permissive licenses are also known as 'Apache-style' or 'BSD-style' and contain minimal requirements about how the software can be modified or redistributed.
This type of software license is perhaps the most popular license used with free and open-source software.
Aside from the Apache License and the BSD License, another common variant is the MIT License.
LGPL
The GNU Lesser General Public License (LGPL) allows you to link to open-source libraries in your software.
If you simply compile or link an LGPL-licensed library with your code, you can release your application under any license--even a proprietary license. But if you modify the library or copy parts of it into your code, you’ll have to release your application under similar terms as the LGPL.
Copyleft
Copyleft licenses are also known as 'reciprocal licenses' or 'restrictive licenses'.
The most well-known example of copyleft or reciprocal license is the GPL. These licenses allow you to modify the licensed code and distribute new works based on it, as long as you distribute any new works or adaptations under the same software license.
For example, a component’s license might say the work is free to use and distribute for personal use only. So, any derivative you create would also be limited to 'personal use only'.
Proprietary
Of all types of software licenses, this is the most restrictive.
The idea behind it is that all rights are reserved. It’s generally used for proprietary software—which is the property of its owner/creator—where the work may not be modified or redistributed.
Reasons why you should use licensed software
Using software that is not licensed is against the law
Before using or buying software, it is important to understand its laws. A software license is a legal requirement for any consumer wishing to use computer software. Failure to have a license when using the software breaches copyright law and can land you or your business in danger of being prosecuted or fined.
Therefore, all software should be legally licensed before it is used.
Software licenses can be overwhelming and confusing to decipher, but you must read them to uncover the exact terms of the license and its restrictions.
Most software licenses are a single-user only, so if it is detected that more than one person is using the same software, your software license can be revoked, and your account could be deactivated.
Therefore, if you want to purchase Microsoft Office software, for example, it is important that you do so from a credible and reliable source to save you from encountering these problems.
The right software license can save you money
When you purchase software, it usually comes with a single-user license.
While it is important to note that a single-user license can sometimes be used across multiple devices that are owned and used by one individual (refer to the specific Terms and Conditions to be sure of this). It is not allowed, lawfully, to be redistributed or used by multiple people.
Therefore, if multiple people need to be using the software, you might consider purchasing multiple software packages, each with its single-user license, but this can be expensive. So, by researching and finding suitable software packages for multi-users, depending on how many users you wish to grant access to the software, you can save money overall.
For instance, you can purchase Microsoft Office Professional 2019 with one license for around $299.99 or buy a multi-user license covering 2 PCs for $449.00--cheaper than buying 2 licenses individually.
Large businesses or schools will be better off looking into volume-licensing a program for when multiple product licenses are needed, but not necessarily multiple copies of the software. These are usually discounted at a reasonable price.
The same goes for students at universities and colleges, as a single-user license cannot be used across a whole course or year group, for example, but would require a volume-licensing program.
Receive around-the-clock license support
Microsoft Office licensed software comes with 24/7 tech support, so whatever your query regarding your software or license, you can access help quickly.
Licensing support for Microsoft Office doesn’t stop at Windows. Even if you are an Apple user, you shouldn’t rule out the importance of getting acquainted with software licensing.
For example, it isn’t uncommon that Mac users are unsatisfied with the alternative apps provided by Apple that replicate Microsoft Office programs. Still, sometimes Microsoft software is not designed to be compatible with Apple-like. It is only compatible with Windows.38
Knowledge check
Complete these three activities.
Instructions:
- Create a comparison of specifications between the latest macOS and Windows OS.
- Research the minimum and recommended systems as well as hardware requirements.
- Put together your findings and then share, discuss, and compare with your peers in the Activity Forum.
Every digital device needs an operating system to manage all the resources that the device can access, such as CPU tasks allocation, memory management, file storage, and access to peripherals. The operating system is also responsible for providing an interface for the user, which is important because it allows users to run applications. One of the main advantages of a graphical user interface (GUI) is that it provides an intuitive and user-friendly way to interact with the operating system and run applications.
For example, an Apple TV device is not suitable for use as a fitness monitor because it lacks the necessary physical sensors or size. However, it is well-suited for entertainment purposes, as it can stream services like Netflix, TVNZ on demand, and others. The operating system on an Apple TV is designed to make it easy for users to select the service they wish to watch, with a GUI that provides an intuitive way to navigate through options.
Similarly, devices like Fitbit and Apple Watch have their own specialized operating systems, designed to make them easy to use for their specific purposes. The GUI on these devices provides an intuitive and visual way for users to access and interact with their fitness data, monitor their health metrics, and receive notifications from their phones.
Embedded systems are specialized computer systems designed to perform specific functions or control specific hardware devices. These systems are often used in devices like appliances, cars, and medical equipment, where the operating system and hardware are tightly integrated to perform a specific task.
In some cases, these embedded systems do not use graphical user interfaces (GUIs) because the devices are not intended for human interaction. For example, a thermostat may use a simple, text-based interface to allow the user to adjust the temperature settings, but it does not require a GUI because it is a standalone device that does not need to display complex graphics or multimedia content.
Instead, embedded systems typically use command-line interfaces (CLIs) or other text-based interfaces or control buttons that allow users to input commands or receive feedback from the system. These interfaces are typically simpler and more lightweight than GUIs, which makes them ideal for use in embedded systems with limited resources.
In summary, an operating system is essential for every digital device, and a GUI provides an intuitive and user-friendly way for users to interact with the operating system and run applications. The examples of Apple TV, Fitbit, and Apple Watch demonstrate how specialized operating systems and GUIs can be tailored to specific user needs and make devices more accessible and easier to use.
On two of your devices, find as many ways as you can to access the settings or preferences of the operating system.
- How many ways did you find?
- How do you usually access the settings or preferences?
Microsoft usually has at least three ways to get to something. Why do you think that Microsoft developed so many different ways?
- Do any of your friends or family else use the same methods as you to access Settings?
Share your results in the Activity Forum post or in Live Sessions with your tutor.
