Security controls are an integral part of any organization's security strategy. They help reduce risk by minimizing the attack surface and addressing vulnerabilities. Security controls can include technical measures, such as firewalls and encryption, and nontechnical measures, such as employee training and awareness. Security controls can help protect an organization's valuable assets and data from unauthorized access, theft, and destruction when implemented correctly.
Security Control Categories
It is common to identify that many security controls are deployed quickly, often as a reactive response to newly identified threats. In the early years of cyber defense, this approach was practical. For example, firewalls provided quick and effective protection and were straightforward to deploy; the level of protection a simple firewall provided was much more comprehensive compared to what is needed today. As viruses and worms began to infect computer systems through the 1990s, organizations deployed antivirus software on workstations and servers. This approach was simple, effective, and solely focused on preventative measures. At the time, this approach worked.
As modern cyber threats have become increasingly sophisticated, the ability to implement relatively simple controls with high levels of protection is becoming much rarer. Current infrastructures are complicated and require layered security controls deployed in a structured and systematic way. Additionally, in the early years of computing, organizations were far less dependent on technology resources, and technology risks were less severe.
A modern approach to security requires integrating several different types of controls, not only preventative but also detective, corrective, compensating, and responsive. Several standards and frameworks exist to help practitioners better understand practical control types. Some examples include NIST Special Publication 800-53 Security and Privacy Controls for Federal Information Systems and Organizations , NIST Special Publication 800-171 Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations , the ISO 27001 standards , and the CIS Controls.
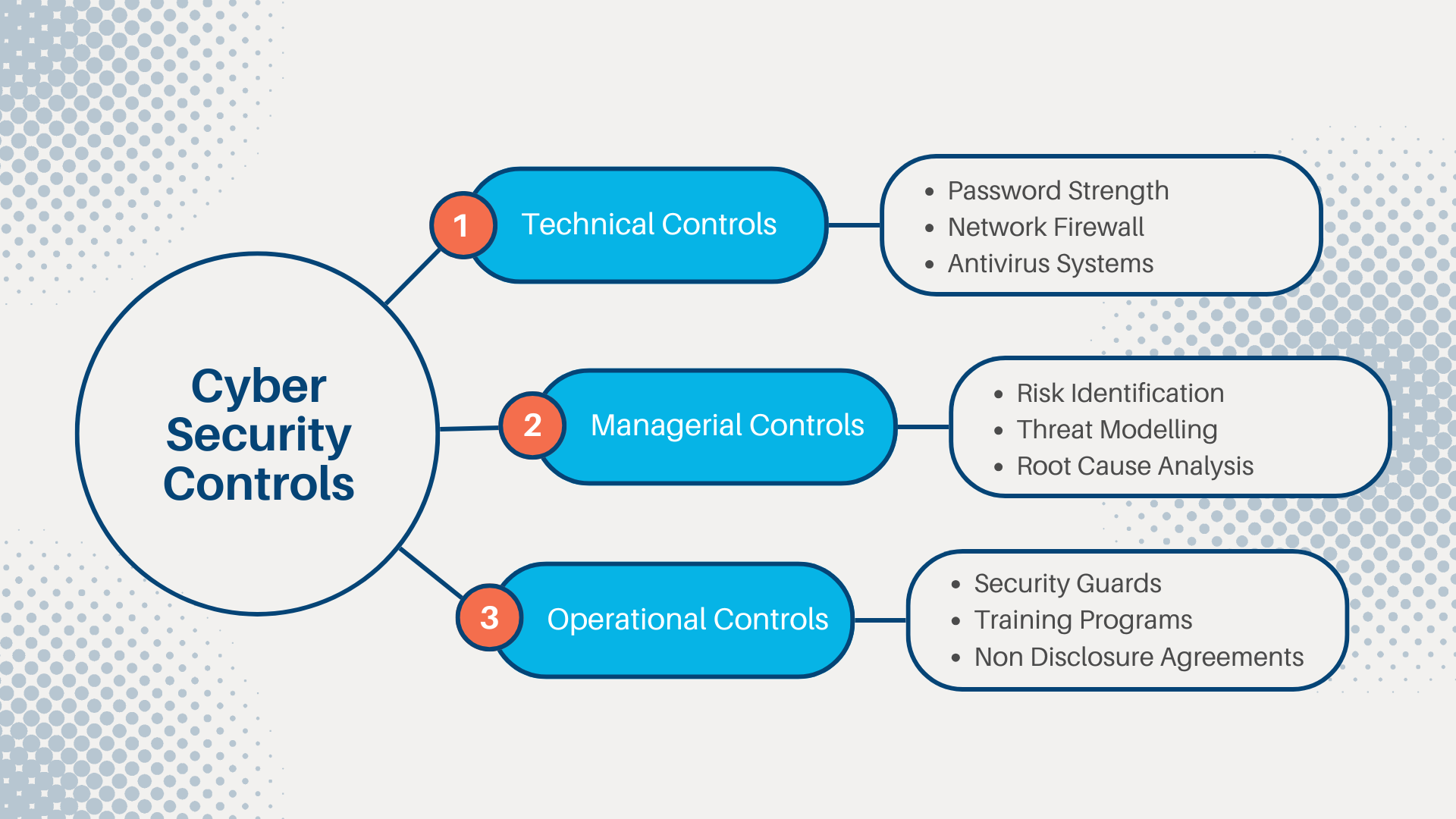
Each control is also organized into different classes, based on the dominant characteristics of the control. The three classes are as follows:
Technical
The control is implemented as a system (hardware, software, or firmware). For example, firewalls, antivirus software, and OS access control models are technical controls. Technical controls may also be described as logical controls.
Operational
The control is implemented primarily by people rather than systems. For example, security guards and training programs are operational controls rather than technical controls.
Managerial
The control gives oversight of the information system. Examples could include risk identification or a tool allowing the evaluation and selection of other security controls.
The significance of these classes is that they are referenced when measuring how effectively assets are protected. The objective is to implement controls in each of the three classes; for example, to identify that a system is protected by preventative, detective, corrective, compensating, and responsive controls in each of the three classes.
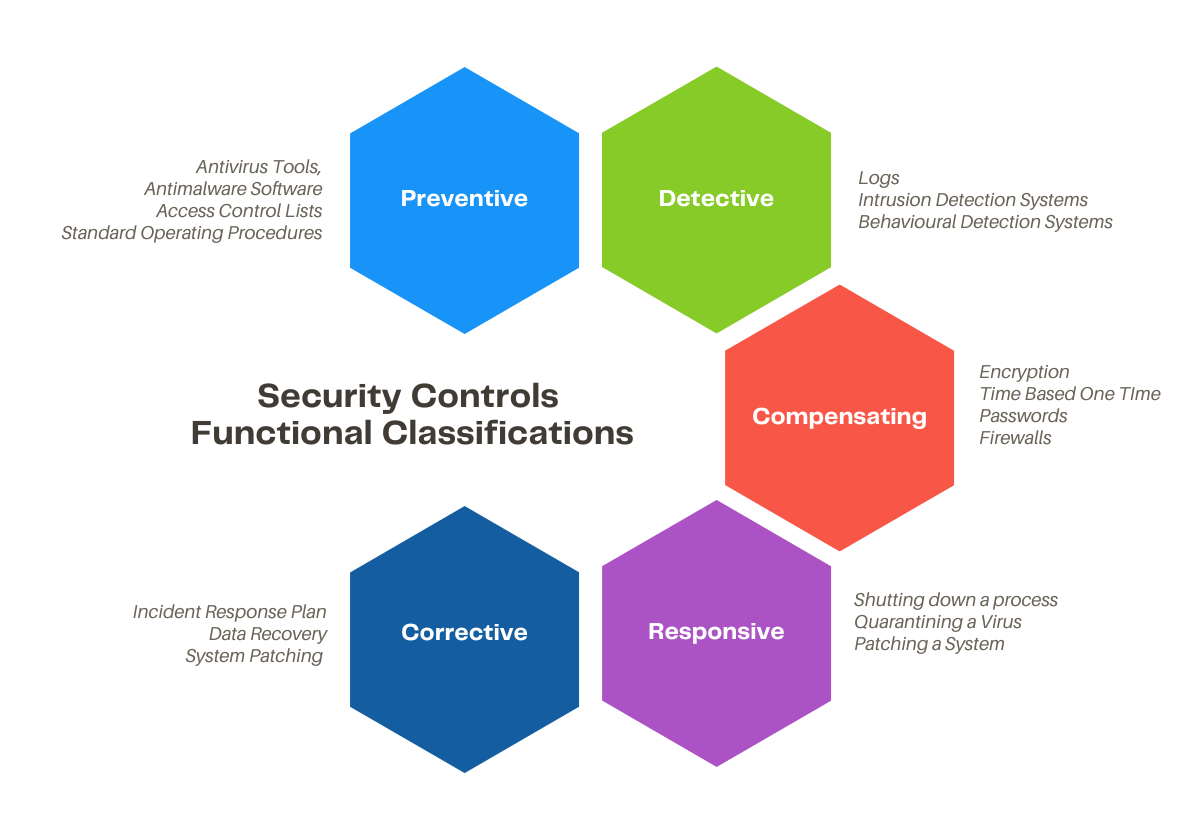
Security Controls Functional Classifications
However they are classified, as a category or family, controls can also be described according to the goal or function they perform:
Preventative
The control acts to eliminate or reduce the likelihood that an attack can succeed. A preventative control operates before an attack can take place. Access control lists (ACL) configured on firewalls and file system objects are preventative-type controls. Antimalware software also acts as a preventative control, by blocking processes identified as malicious from executing. Directives and standard operating procedures (SOPs) can be thought of as administrative versions of preventative controls.
Detective
The control may not prevent or deter access, but it will identify and record any attempted or successful intrusion. A detective control operates during the progress of an attack. Logs provide one of the best examples of detective-type controls.
Corrective
The control acts to eliminate or reduce the impact of an intrusion event. A corrective control is used after an attack. A good example is a backup system that can restore data that was damaged during an intrusion. Another example is a patch management system that acts to eliminate the vulnerability exploited during the attack.
Compensating
The control serves as a substitute for a principal control, as recommended by a security standard, and affords the same (or better) level of protection but uses a different methodology or technology.
As no single security control provides complete protection, each is like a link in a chain, with each control contributing to the overall strength of the chain. A link's weakness impacts the overall effectiveness of the chain, but unlike an actual chain, a failure in one control should not result in a complete loss. It might be practical to think of each control type as an individual chain comprised of a series of individual controls of that same type.
Often overlooked and underestimated, responsive controls are designed to assist in the event of an incident. Protection and detection go a long way to defend a network, but at some point bad things are going to happen. Without responsive controls, a security event can spiral out of control very quickly.
Responsive
These controls serve to direct corrective actions enacted after an incident has been confirmed. In a Security Operations Center (SOC), responsive controls might include several very well-defined actions to be taken by an analyst after identifying a specific issue. These actions are often documented in a playbook.
Adopting a functional approach to security control selection allows you to devise a Course of Action (CoA) matrix that maps security controls to known adversary tools and tactics, matching your cybersecurity defensive capabilities to the offensive capabilities of potential cyber adversaries.
Prioritization & Escalation
Vulnerability response prioritization and escalation are integral to managing security risks. After identifying vulnerabilities, they must be classified according to their severity and potential impact on the organization. Vulnerabilities with the highest severity and potential impact must be prioritized and addressed first, while those with lower severity and potential impact can be addressed later. It is also important to ensure that any high-severity vulnerabilities are escalated to all relevant stakeholders to ensure they are informed and can contribute to the response as necessary. Additionally, it is vital to have an established process for escalating vulnerabilities in case the severity of the vulnerability changes or the vulnerability is exploited before remediations are implemented.
Managing Attack Surfaces
As previously described, threat models are valuable tools that allow a system to be deconstructed into its functional parts to understand better how a threat actor might exploit it. Furthermore, threat models seek to identify which threat actors are likely to attempt to exploit the system. The goal of the threat model is to help determine how to improve a system's security posture, and part of this exercise often includes attack surface management and hardening.
An attack surface describes all potential pathways a threat actor could use to gain unauthorized access or control. Each piece of software, service, and every enabled protocol on an endpoint offers a unique opportunity for attack. Removing or disabling as many of these as possible can significantly reduce the number of (potentially) exploitable pathways into a system. Additionally, default configurations typically favor functionality and compatibility over security, so it is essential to understand how to customize a system to allow for the most secure type of operation, not necessarily the most convenient. Several hardening guides are available that outline secure configurations in precise detail. Two popular sources of best practice configuration include the Center for Internet Security Benchmarks™ and the Department of Defense's Security Technical Implementation Guides (STIGs.) As of this writing, the CIS Benchmark for Windows 10 had over 1,000 pages of recommended configuration changes!
 Further Learning Resources: DoD STIGs CIS Benchmarks™
Further Learning Resources: DoD STIGs CIS Benchmarks™
An organization's attack surface is broad, and every asset is interconnected. The overall attack surface is composed of every asset's attack surface. To keep this in perspective, every on-premises device, cloud resource, external service (i.e., software as a service (SaaS), online storage, or software repository), or external network configured to access the organization is part of the attack surface. Attack surface management describes the methods used to continuously monitor an environment to quickly identify changes to its attack surface. This type of monitoring seeks to continuously locate shadow-IT and other unknown devices, weak or default passwords, misconfigurations, missing patches, and many other items of concern.
Managing the Attack Surface
Managing the attack surface means maintaining awareness of exposed services and ensuring they operate securely per organizational policy. Maintaining awareness necessitates continuous discovery and routine evaluation of configurations to ensure they are secure and working as intended. The most attack-prone area of an organization's infrastructure is the edge, which includes any services exposed to the Internet. In 2007, a University of Maryland study identified that Internet-connected services experience an attack every 39 seconds, and these numbers are likely worse today . With these numbers in mind, it is critically important to quantify services exposed to the Internet and to identify any changes to this footprint quickly.
Passive discovery can be a practical approach to managing the attack surface. Passive discovery describes the methods used to identify systems, services, and protocols indirectly. Passive discovery, such as network packet capture, can reveal information about network-connected hosts, communications channels, protocols in use, and activity patterns. Passive discovery is beneficial as it leverages careful observation to show characteristics of network-connected software and devices.
Edge discovery seeks to define the "edge" of the network fully. It is easy to assume that the edge is composed only of Internet-facing servers. The edge is instead composed of every device with Internet connectivity. Assuming that attacks will occur from the Internet, anything accessible to it must be considered as part of the edge. The US Cybersecurity & Infrastructure Security Agency (CISA) identified that 90% of successful cyberattacks start with a phishing email. This fact underscores that an organization's edge is much broader than is often assumed.
Evaluating the Attack Surface
Sometimes, security controls do not operate as expected; therefore, it is crucial to perform testing to ensure that they are working correctly. Also, security controls are often modified or disabled by support staff while working to resolve trouble tickets. For these reasons, a testing plan must be in place and designed to validate controls are functioning as intended. For example, validating that firewalls only allow the right traffic to pass, that endpoint protection is operating properly on employee workstations, and that web application firewalls correctly identify and block injection attacks name just a few.
Not all control weaknesses or misconfigurations are easy to identify. In the same regard, having confidence that sufficient controls are in place is challenging. Leveraging the analytical skills of an expert practitioner is irreplaceable. Adversary emulation, penetration testing, and bug bounty programs are all designed to assess an organization's security posture as thoroughly as possible. A penetration test involves hiring a trusted offensive security expert to fill the role of an attacker, tasking them to exploit the environment and evaluate the effectiveness of existing protections. The penetration test includes a findings report crafted with details regarding identified weaknesses and recommended remediations. Another type of penetration test, referred to as adversary emulation, seeks to mimic the actions of known threat actor groups. The MITRE ATT&CK® framework typically forms the basis of this type of assessment. After a threat assessment identifies threat actor groups, the ATT&CK framework provides details regarding their tactics, techniques, and procedures (TTPs). Emulating these TTPs helps assess whether existing protections are sufficient to stop attacks characteristic of the threat actor.
One last assessment method involves offering rewards for responsible disclosure of vulnerabilities. Bug bounties allow organizations to define areas of their environment they would like help protecting. The bug bounty identifies elements of the environment that are in scope for testing and the rewards available for reporting issues. This approach incentivizes offensive security professionals to assess controls on an ongoing basis and can also help identify unknown and undocumented vulnerabilities. Bugcrowd and HackerOne are popular bug bounty platforms.
Penetration Testing and Adversary Emulation
Penetration testing and adversary emulation are techniques used to assess an organization's attack surface and identify vulnerabilities. Both techniques supplement attack surface management and help improve an organization's security posture.
Penetration testing involves simulating an attack on an organization's network to identify vulnerabilities and weaknesses. The goal is to identify the most vulnerable components within an organization's environment and determine how an attacker could exploit them. The penetration test results are then used to prioritize risk mitigation efforts and reduce the attack surface.
Adversary emulation, on the other hand, involves simulating a real-world cyber attack by an actual adversary to assess an organization's defenses. This technique involves a more comprehensive and realistic simulation of a targeted attack. The goal is to identify gaps and weaknesses in an organization's security infrastructure that a known threat actor typically targets. Doing so helps the organization improve its ability to detect and respond to specific attacks associated with the threat actor instead of generalized attacks used in penetration testing.
Organizations can reduce their risk of a successful cyber attack by identifying and mitigating vulnerabilities before attackers exploit them. Attack surface management provides a framework for organizations to assess and manage their attack surface, and penetration testing and adversary emulation are techniques used to evaluate the effectiveness of the organization's security measures.
How to Reduce Attack Surface?

