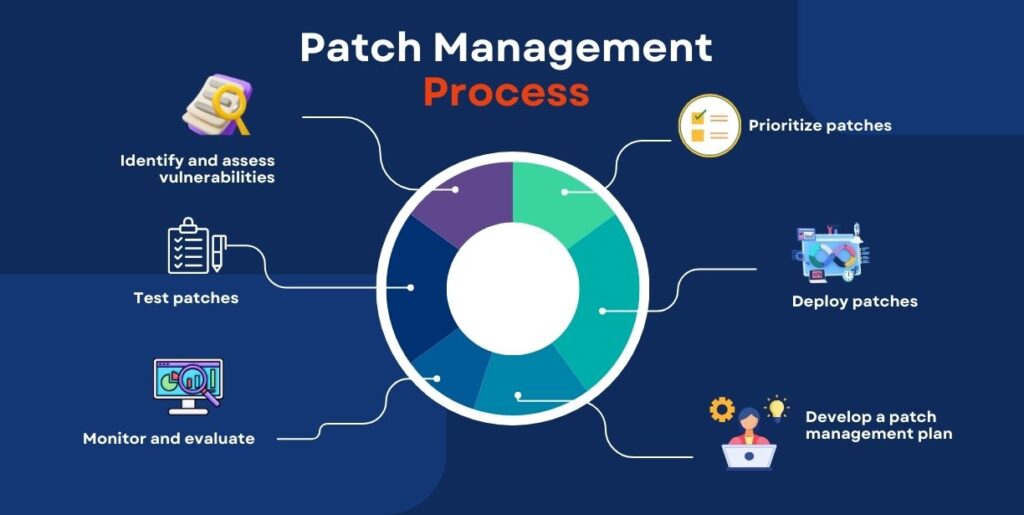
Patch management is an essential part of IT security. It involves regularly monitoring, assessing, and updating an organization's software, such as operating systems, applications, and device drivers. Patch management aims to ensure organizations have the latest security updates and patches to protect their systems from potential vulnerabilities. It should also include a plan for applying these patches promptly and a backup plan in case of disruptions. Patch management requires an ongoing effort, but it is an integral part of an organization's security posture.
Software Patching and Host Protections
The volume of software vulnerabilities and related patches and updates continues to expand at an ever-increasing pace. Managing and applying patches is time-consuming and necessitates a centralized patch management system.
Patches are inevitable and apply to a wide variety of operating systems, application software, cloud instances, and device firmware. Patch management can be a manual process, an automated process, or a combination of both. Patch automation is essential but often requires occasional manual work to address problems related to deployment or installation errors. For example, administrators might develop custom scripts designed to help patch management systems more accurately identify missing patches, search for specific hardware information, or gracefully stop and start system services prior to patching.
An effective patch management strategy requires patch management software to be configured based on the risks associated with each system and its applications. Mission-critical systems need to be treated differently than less critical ones to support availability requirements. Desktops are often patched as quickly as possible after a brief testing phase.
Important patch management considerations include the following:
- An individual or task-specific team responsible for reviewing vendor-supplied newsletters and security patch bulletins
- Mechanisms to patch operating systems and all applications running on it, regardless of application vendor
- Patch management principles that incorporate cloud resources
- Assigning updates into urgent, important, and noncritical categories
- A patch test environment where urgent and important patches can be installed and tested and analyzed prior to deployment into production
- Detailed logging designed to support monitoring and troubleshooting of patch deployment activities
- A method to evaluate firmware updates prior to deployment
- Immediate push delivery of critical security patches
- A routine schedule for the rollout of noncritical patches
Patch testing aims to determine whether a software patch creates problems with the organization's unique mix of hardware, software, and configuration settings. Patch testing should primarily involve testing a patch on a single isolated system to determine whether a patch causes problems, such as software crashes or system instability. Additionally, testing should validate that issues addressed by the software patch work as expected—for example, a patch successfully removes a vulnerability. A common way to test a patch is by setting up a non-production environment hosting like-for-like mission-critical applications, including enterprise applications and networking systems (where available). Doing this allows patches to be deployed by infrastructure teams, validated by software support staff, and assessed by security teams before deployment into the production environment. Additionally, vulnerability scans should verify that patches only resolve vulnerabilities and do not introduce any new ones!
Image of AWS Patch Manager compliance report.
Description
The report has three major sections from top to bottom. A header at the top reads \Patch Compliance.\"The first section has text that reads, Patch compliance reporting allows you to view compliance information across a number of different axis. Select the report type below. Below, there are two lines each with an option selected in a drop-down menuLine 1: Report Type, with Patch Groups selected.Line 2: Patch Group, with Windows server 2016 Base selected.The second section is titled \"Compliance Summary.\" Below, three boxes read: 3 Instances are up to date.
Control over endpoint configuration is the role of centralized configuration management systems. Centralized configuration management plays a critical role in infrastructure as code, CI/CD, and DevOps environments but also plays a vital role in traditional environments. A centralized configuration management system allows an administrator to define device configuration settings on a management server and then push the settings to endpoints in an automated way.
Centralizing configurations enables consistency as the configuration is defined once and applied to many systems. Additionally, the configuration is enforced, meaning the central management server will overwrite changes made to an individual endpoint's configuration. As a result, the central management server can provide near real-time visibility into configuration changes. Near-real time visibility into device configurations enables continuous compliance monitoring. When a secure configuration is centrally configured and controlled in this way, any changes to it (on an endpoint) will generate an immediate alert.
Examples of configuration management tools include the following:
Chef
Puppet
Ansible
Terraform
Image of Chef iptables cookbook.
Description
This diagram shows a Chef cookbook for the iptables firewall software. Chef cookbooks include everything needed to install and configure the software. Cookbooks are often shared to benefit the community of Chef users.
A header at the top reads "Chef Supermarket." There are 3 sections below this.
The first section has a header that reads "iptables" by a drop-down menu for 41 versions, with 8 dot 0 dot 0 selected. The text below reads, Installs the iptables daemon and provides resources for managing rules. Below this, the three-tab menu from left to right represents PolicyFile, Berkshelf, and Knife. The PolicyFile tab is open and consists of one line of command line code.
The second section has a menu tab from left to right that represents Readme, Dependencies, Changelog, and Quality 50 percent. The Readme tab is open. The section below is titled "iptables cookbook" and reads, Install iptables and provides a custom resource for adding and removing iptables rules. Below this are several Platforms under Requirements.
A section to the right side of the page includes details about the date updated, Supported Platforms, and the License and a button labeled "Download Cookbook."
Understand Maintenance Window
Many organizations adopt routine maintenance windows so administrators can perform maintenance tasks during these pre-established times. Maintenance windows enable preventative maintenance and consistent deployment of noncritical patches. All work planned during maintenance windows should comply with change management policies. Computers and devices are often restarted during maintenance windows, and various services are also modified, restarted, and added. Monitoring infrastructure must be able to correlate events like these to a scheduled maintenance window to adjust alert severity ratings.
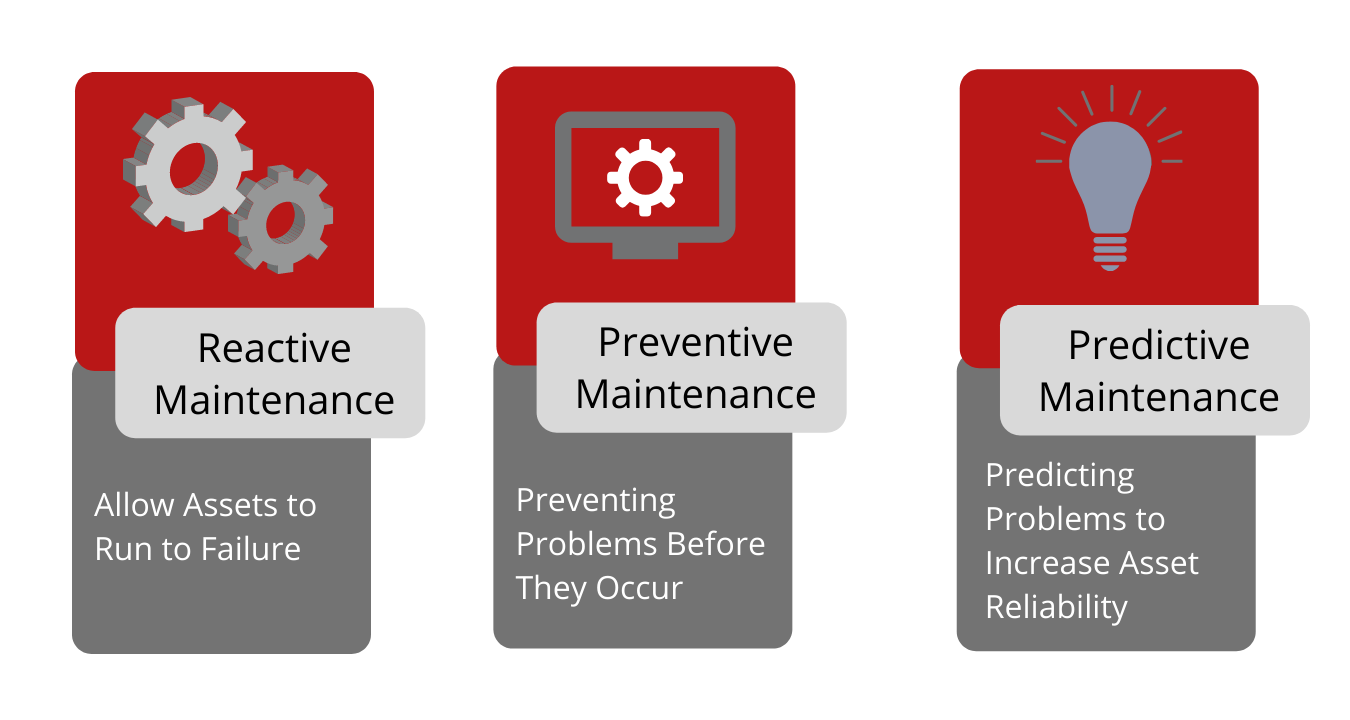
Preventive and Predictive maintenance are also classified under Proactive Maintenance
Analysis of events occurring during maintenance is essential, as a savvy attacker might try to avoid detection by performing actions during these times. Knowing what will happen in a maintenance window is critical to help discern between authorized and unauthorized events. A poorly planned and managed maintenance window can be a nightmare for the SOC as it tries to manage a sudden surge in alerts and warnings generated by numerous services as they are added, modified, and restarted!
Patch management teams rely on maintenance windows to complete patch rollouts. The duration of the maintenance window can be a significant constraint. Change management policy dictates that patching must finish quickly enough to accommodate rollback plans if trouble occurs—without overrunning the maintenance window. Change management rollback is the process of undoing a system's changes to restore the system to an earlier, pre-change state. Rollbacks can be performed manually or automatically, depending on the system, and are done to return a system to its previous state. The need for a rollback is not always obvious. Even after passing initial tests, some changes introduce issues that may not become apparent until after a system is subjected to heavy workloads or scenarios that are not easy to test. After changes have been made to a system, analysts must monitor it to verify it is operating as expected. Monitoring often involves log monitoring (looking for errors or warnings) and performance monitoring (comparing characteristics against an established baseline).
