Active threats represent risks to business operations that need to be identified and monitored. Open-source intelligence (OSINT) and threat-intelligence sharing platforms are highly effective ways to do this. With OSINT, a wide range of publicly available information is collected and analyzed to identify potential threats. OSINT sources are diverse and include social media, blog posts, news articles, chat forums, and many other sources. Once potential threats are identified, threat-intelligence sharing platforms can help identify specific details about them, such as origin, methods, and potential targets, and track how they evolve. Using OSINT and threat-intelligence sharing helps organizations stay ahead of active threats and protect their operations.
Open Source Intelligence
Reconnaissance is often the precursor to more direct attacks. Understanding reconnaissance techniques and applying them to your own company and networks will reveal how much useful information is being unintentionally provided to threat groups. You can also use reconnaissance as a counterintelligence tool to build up profiles of potential or actual adversaries.
Most companies and their employees publish vast information about themselves online via blogs and social media sites. Some of this information is published intentionally; much is released unintentionally and exploited in unexpected ways. Attackers often "cyber stalk" their victims to discover information about them via Google™ Search or other tools. Open-source intelligence (OSINT) refers to publicly available information and associated tools for aggregating and searching it.
OSINT can allow an attacker to develop any number of strategies for compromising a target. Locating an employee on a dating site might expose opportunities for blackmail or entrapment; finding an employee looking for a secondhand laptop or mobile device on an auction site might allow an attacker to get a compromised device into the employee's home or workplace. Knowing the target's routine or present location might facilitate break-in or theft, or create an opportunity for some sort of social engineering.
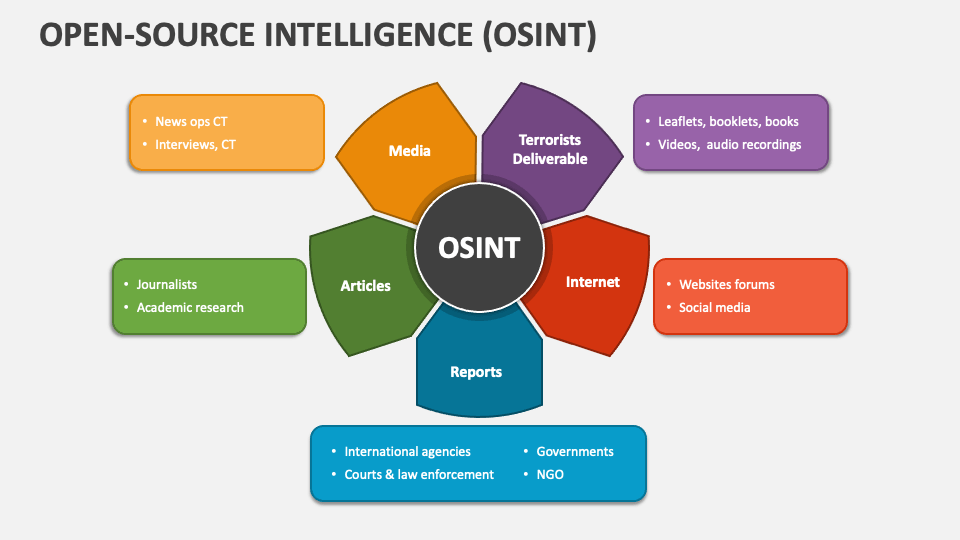
Some sources of OSINT include the following:
- Publicly available information—An attacker can harvest information from public repositories and web searches. Available information includes categories such as the IP addresses of an organization's DNS servers; the range of addresses assigned to the organization; names, email addresses, and phone numbers of contacts within the organization; and the organization's physical address. This data is publicly available through Whois records, Securities and Exchange Commission (SEC) filings, telephone directories, and more.
- Social media—Attackers can use social media sites like Facebook and LinkedIn to find an organization's information. Depending on how much an organization or an organization's employees choose to share publicly, an attacker may find posts or user profiles that give away sensitive information or simply act as another vector or target for the attacker to take advantage of.
- HTML code—The HTML code of an organization's web page can provide information, such as IP addresses and names of web servers, operating system versions, file paths, and names of developers or administrators. The layout and organization of the code can reveal development practices, capabilities, and level of security awareness.
- Metadata—Attackers can run metadata scans on publicly available documents using a tool like Fingerprinting Organizations with Collected Archives (FOCA). For example, Microsoft Office documents posted on the Internet may not directly divulge sensitive information about an organization, but an attacker could extract useful information from its metadata, including the names of authors or anyone that made a change to the document. By using search engines, FOCA (https://github.com/ElevenPaths/FOCA) can cross-reference files with other domains to find and extract metadata.
Defensive OSINT
Defensive OSINT is a type of intelligence gathering that focuses on identifying threats before they occur. It also helps create a strategy to minimize the impact of an attack before it occurs. The most critical component of defensive cybersecurity OSINT is identifying potential attackers and their attack methods beforehand.
Some sources for Defensive OSINT include the following:
Government bulletins
The government is responsible for protecting the country's constituents and the national infrastructure and publishing a wide variety of information and advice regarding observed threats. For example, the Department of Homeland Security and the Cybersecurity and Infrastructure Agency publish several types of cybersecurity guidance, including basic informational content and binding operational directives that federal agencies must implement.
CERT
The goal of a computer emergency response team (CERT) is to mitigate cybercrime and minimize damage by responding to incidents quickly. They work with local law enforcement, federal agencies, and other organizations to help prevent cyberattacks. CERTs coordinate responses to major events like natural disasters or terrorist attacks. Because of this, CERTs can provide knowledge and information regarding trending and observed attacks.
CSIRT
A computer security incident response team (CSIRT) is a group responsible for responding to security incidents involving computer systems. The team typically consists of information security professionals, network administrators, system administrators, legal representatives, and other stakeholders. The team’s goal is to respond to security incidents quickly and effectively while minimizing the impact to the organization.
Deep/Dark web
The dark web serves as an operating platform for many cybercrimes. Threat actors utilize the dark web to organize their efforts and sell products such as credit card numbers, drugs, weapons, and malware. Observing this activity can provide insight to threat actor activities, future attacks, information regarding current tactics, and evidence of previously undiscovered breaches.
Internal sources
It is important to consider that evidence regarding active threats, reconnaissance activities, and suspicious behavior exists within the environment being protected. Activity logs are a goldmine of information and operational insight and must be continuously collected and analyzed.
Proprietary/Closed Source Intelligence
Threat intelligence data refers to information collected, analyzed, and contextualized to identify and assess potential security threats. Data can come from various sources, including open-source, human, and technical intelligence. Threat intelligence data is categorized into two broad types: strategic and operational. Strategic threat intelligence provides a high-level view of the threat landscape, including emerging trends, tactics, and techniques threat actors use. On the other hand, operational threat intelligence provides more granular details about specific threats, such as indicators of compromise, malware analysis, and network forensics. The ultimate goal of threat intelligence data is to provide actionable insights and recommendations that organizations can use to protect themselves against potential security threats better.
Threat intelligence data depends on three important attributes timeliness, relevancy, and accuracy which are described in the following table.
Threat intelligence is very widely provided as a commercial service offering, where access to updates and research is subject to a subscription fee. Some of these commercial sources primarily repackage information coming from free public registries, while others provide proprietary or closed-source data that may not be found in the free public registries. Closed-source data is derived from the provider's own research and analysis efforts, such as data from honeynets that they operate, plus information mined from its customers' systems, suitably anonymized. Most of the commercial feed (sometimes referred to as a paid feed) providers also market their own platform for processing and disseminating threat intelligence. There are also platform providers who do not produce their own security feeds. Some examples of commercial providers include the following:
Information Sharing and Analysis Centers (ISACs)
Information Sharing and Analysis Centers (ISACs) provide critical infrastructure owners and operators with cybersecurity information and services. They facilitate the sharing of threat information and best practices between the public and private sectors, allowing for the protection of vital assets. ISACs also provide advice on current and emerging cyber threats, helping to ensure a more secure cyber landscape. .
 Reading Resource: More information regarding ISACs
Reading Resource: More information regarding ISACs
Information Sharing and Analysis Centers
Since the 1990s, governments have mandated that industries where cyberattack poses risks to life or health or to national security must form public/private partnerships and industry associations to disseminate sector-specific threat intelligence. For each critical industry, Information Sharing and Analysis Centers (ISACs) have been set up. Where a generic open-source or commercial threat intelligence provider might use corporate or academic networks to gather data, ISACs produce data from their members' systems, so the data is highly industry-specific and relevant. Information shared within an ISAC is given legal protections by the PCII program operated by the Department of Homeland Security (DHS) (dhs.gov/cisa/pcii-program). A list of all US-based ISACs is available at nationalisacs.org/member-isacs-3. In the UK, the Cyber Security Information Sharing Partnership (ncsc.gov.uk/section/keep-up-to-date/cisp) serves a similar purpose.
Threat Intelligence Sharing Benefits
Threat intelligence sharing helps improve several aspects of cybersecurity, including incident response, vulnerability management, risk management, and security engineering.
 Critical Infrastructure
Critical Infrastructure
The DHS identifies 16 critical infrastructure sectors such as communications, energy, water, nuclear reactors and waste, emergency services, and so on. Each sector is supported by its own ISAC. One of the primary areas of focus for cybersecurity in industries that support critical infrastructure is with embedded systems and industrial control systems.
Government
The Multi-State ISAC serves nonfederal governments in the US, such as state, local, tribal, and territorial governments. One of the key cybersecurity concerns for governments is interference in the electoral process and the security of electronic voting mechanisms. In fact, there is an ISAC dedicated to election infrastructure security issues.
Healthcare
Healthcare providers are targeted by criminals seeking blackmail and ransom opportunities by compromising patient data records or by interfering with medical devices.
Financial
The financial sector is an obvious target for fraud and extortion. Attackers can target both individual account holders and financial institutions themselves. Serious financial shocks, such as major trading platform or ATM outages, can also pose a national security risk.
Aviation
As with most commercial industries, the aviation industry is targeted for fraud, but there are also substantial risks from terrorists or hostile nation-state actors seeking to disrupt services or cause casualties. Air traffic control and the safe operation of aircraft depends on many interconnected systems, some of which use aging infrastructure or technology that is susceptible to interference and spoofing, such as radar and GPS.
Threat Intelligence Sharing
Threat information sharing is crucial for cyber defense teams and cybersecurity organizations. Cyber threat intelligence sharing focuses on finding indicators of compromise, tracking threat actor groups, documenting findings, discussing strategies, and distributing this knowledge.
Many leading cybersecurity vendors openly share threat information via the Cyber Threat Alliance (CTA). One of the most critical tactics to help bolster defensive team capabilities and effectiveness is participating in an industry group that actively shares information on threats and attacks.
An effective threat information platform enables the analysis and distribution of IOCs, tactics, techniques, and procedures (TTPs), threat actors, courses of action, incidents, and other types of similar information. These details are shared in real time using machine-readable formats such as the Trusted Automated eXchange of Indicator Information (TAXII) message exchange and Structured Threat Information eXpression (STIX) formats. This type of information sharing helps support incident response teams, risk managers, security engineers, and security and vulnerability analysts by providing context and descriptions of the attacks they should prepare for and seek to identify. Focusing detection and monitoring activities in this way can help reduce detection times and vastly improve monitoring effectiveness by assisting teams to focus on high-probability issues.
Confidence Levels
This type of strategic intelligence provides deep insight into broad-based or longer-term trends. It provides early warning about threats to help leaders understand the risks that cyber threats pose to their organizations. Additionally, threat feed information helps craft alerts and search for relevant security incidents using rule templates based on imported threat intelligence.
Threat intelligence analysts use threat information to develop confidence levels that help reduce noise and prioritize highly relevant and targeted activities. Platforms like MISP implement taxonomies called Admiralty-Scale or Estimative-Language to help analysts develop and describe confidence levels for different types of threat information.
 More information about the MISP Threat Sharing platform
More information about the MISP Threat Sharing platform
